What Features to Look for in a Vulnerability Management Tool?
Managing vulnerabilities is key to protecting your organization from threats in cyber security. One effective way to manage vulnerabilities is by using a vulnerability management tool. Thus, knowing what to look for in a vulnerability management tool is essential. This article highlights the crucial features of effective vulnerability management tools and how they can strengthen your organization’s security posture.
What is Vulnerability Management?
I. Definition and Objectives
Vulnerability management is the ongoing process of identifying, assessing, and mitigating security weaknesses in your IT environment. The primary goals of vulnerability management are:
- Identifying Vulnerabilities: Discovering security gaps and flaws through scans and threat intelligence.
- Assessing Impact: Evaluating the severity and potential impact of identified vulnerabilities on the organization.
- Mitigating Risks: Implementing fixes to address these vulnerabilities.
II. Why Vulnerability Management is Important
An effective vulnerability management system is crucial for a strong cybersecurity posture. Regularly finding and fixing vulnerabilities helps reduce risks and prevent issues like data breaches, financial losses, and damage to your reputation. Without proper management, vulnerabilities can be exploited by hackers, leading to serious information security problems.
How Does Vulnerability Management Work?
The Vulnerability Management Process
- Identification: Vulnerabilities are discovered through various methods like automated scans and threat intelligence feeds.
- Assessment: Once identified, vulnerabilities are evaluated for their severity and potential impact. This involves understanding the likelihood of exploitation and the consequences of an attack.
- Prioritization: Not all vulnerabilities are equal. Effective vulnerability management involves prioritizing vulnerabilities based on their risk level and the criticality of the affected assets.
- Remediation: Applying patches, configuration changes, or other fixes to address vulnerabilities. This step often involves collaboration between security and IT teams.
- Verification: After remediation, vulnerabilities are reassessed to ensure that they have been effectively mitigated. This step confirms that the fixes are in place and functioning as intended.
Benefits of Vulnerability Management
I. What is a Vulnerability Management Tool?
A vulnerability management tool is a specialized software designed to automate and streamline the vulnerability management process. It assists in identifying, assessing, and managing vulnerabilities more efficiently than manual methods.
II. Why You Need a Vulnerability Management Tool
- Improved Detection and Coverage: Vulnerability management tools automatically scan and discover vulnerabilities across your network.
- Enhanced Risk Management/Efficient Remediation: By prioritizing vulnerabilities based on risk assessments, these tools help you tackle the most critical issues first.
- Regulatory Compliance: They help meet compliance requirements and maintain audit trails, which are essential for regulatory standards.
- Time and Cost Efficiency: Automation reduces manual effort, accelerates response times, and ultimately saves time and operational costs.
Must Have Features in a Vulnerability Management Tool
Choosing a vulnerability management tool with the right features is crucial for ensuring your organization’s cybersecurity defenses remain robust and responsive. Here are the key features to look for in a vulnerability management tool to maximize its effectiveness and meet your security needs:
- Continuous Scanning
A reliable vulnerability management tool should offer continuous scanning capabilities to ensure that vulnerabilities are identified as soon as they appear. This feature ensures up-to-date protection and timely response to emerging threats, allowing you to stay ahead of potential attackers and mitigate risks before they can be exploited.
Example: 8iSoft YODA’s vulnerability scanning engine operates continuously in the background, running regular scans across your network and assets. It instantly flags new vulnerabilities, allowing your team to respond quickly and effectively.
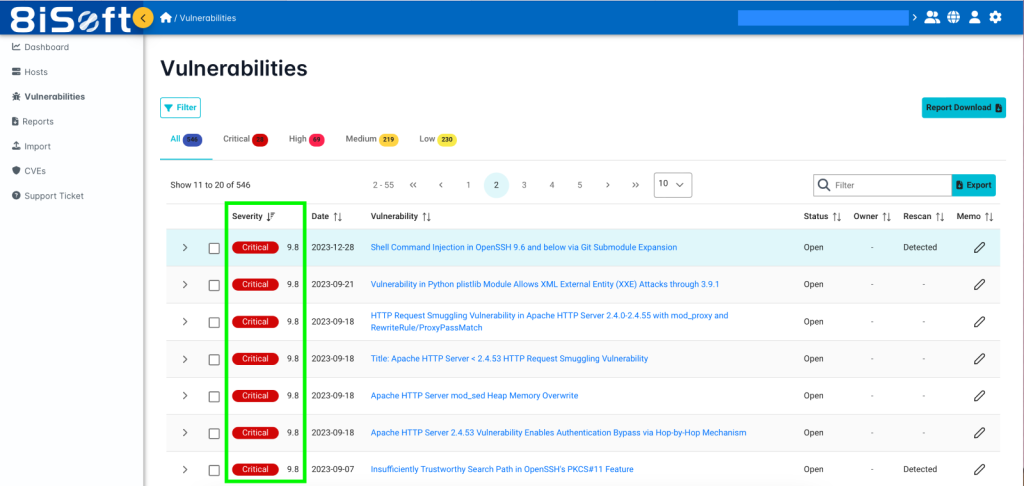
- Prioritization and Risk Assessment
Not all vulnerabilities pose the same level of risk. Therefore, effective prioritization and risk assessment are vital to ensuring that your organization focuses its resources and efforts on the most pressing security issues. Without proper prioritization, your team may waste valuable time and resources addressing low-impact vulnerabilities while leaving critical risks unmitigated. Look for features that assist with:
- Risk Scoring: Look for tools that use established frameworks like the Common Vulnerability Scoring System (CVSS) and leverage the Common Vulnerabilities and Exposures (CVE) database to assign risk scores to vulnerabilities. This helps quantify the severity of each vulnerability based on factors such as exploitability and impact.
- Vulnerability Ranking: The tool should be capable of reporting the status and severity of vulnerabilities. This allows your team to focus on the most critical issues first, ensuring that high-risk vulnerabilities are addressed promptly.
- Clearly Identify Vulnerability Severity Levels: A good vulnerability management tool should feature intuitive dashboards and reports that clearly categorize vulnerabilities by severity. This helps administrators quickly assess and manage vulnerabilities based on their risk levels.
- Overall Health Score: An overall risk score feature, often referred to as a health score, provides a snapshot of the risk levels (low, medium, critical) for all discovered vulnerabilities. This helps organizations balance risk priorities against available resources, facilitating more effective risk management and decision-making.
Example: YODA’s risk scoring and prioritization features allow you to view vulnerabilities ranked by severity and risk impact, including CVE vulnerabilities. This ensures that the most critical vulnerabilities are addressed first, based on their potential impact on your organization.

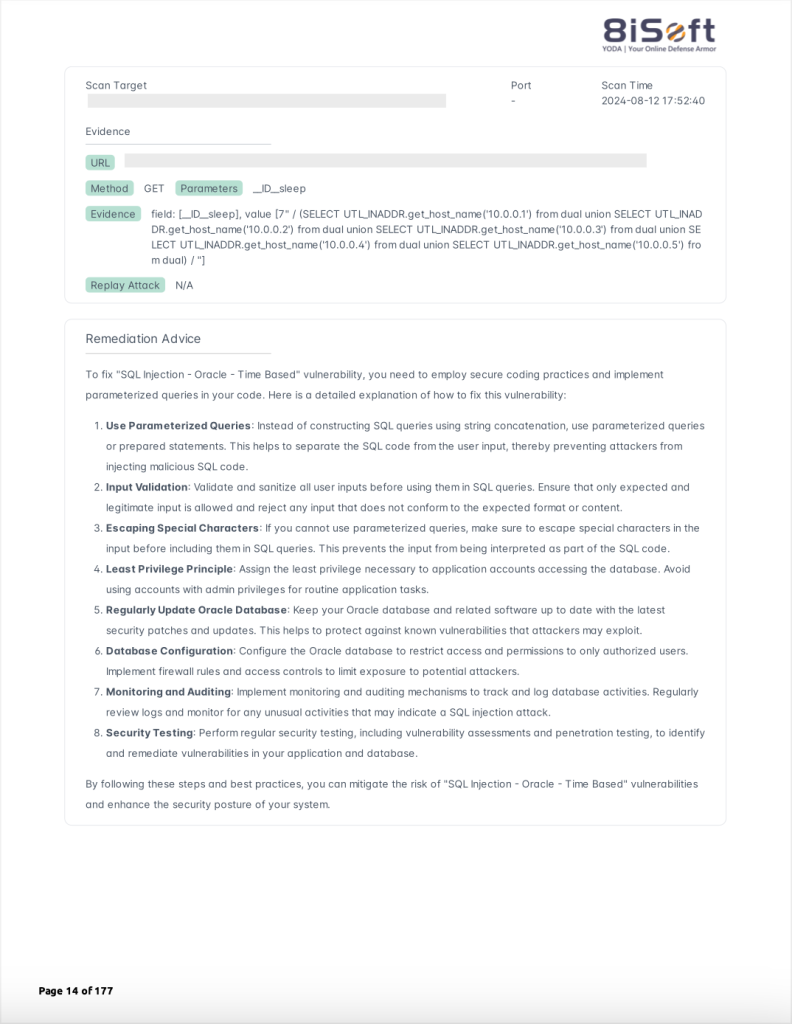
- Remediation Reports
Effective vulnerability management relies on detailed and actionable remediation reports. These should include:
- Total Number of Scans: An overview of how many scans have been conducted.
- Overall Scan Summary: A summary that provides insights into the overall status of vulnerabilities found during scans.
- Recommendations for Remediation: Detailed suggestions for addressing identified vulnerabilities. This helps in planning and implementing effective fixes.
These reports provide a comprehensive overview of your security status, guiding remediation efforts and helping track progress over time.
Example: YODA generates detailed remediation reports that include the total number of scans, an overall summary, and specific recommendations for addressing vulnerabilities, guiding your remediation efforts.



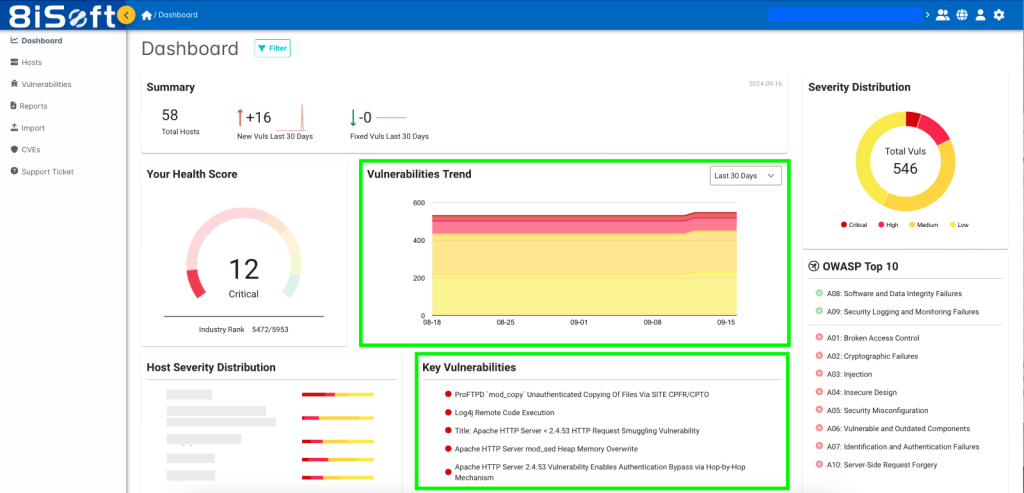
- User-Friendly Interface
Just like other cyber security tools, a vulnerability management tool’s effectiveness is heavily influenced by its user-friendly interface. Key aspects include:
- Intuitive Dashboards: The tool should feature clear visualization of vulnerability data and trends. Intuitive dashboards enable users to quickly understand the current security status and identify areas needing attention.
- Clear and Comprehensive: Dashboards must be easy to navigate and provide a straightforward view of vulnerability data. They should allow administrators to track vulnerability severity levels, view risk scores, and manage policies and scanners efficiently.
- Real-Time Monitoring: Real-time dashboards are vital for monitoring vulnerabilities and tracking remediation progress. They provide up-to-date insights and facilitate immediate responses to emerging issues.
Example: YODA features a user-friendly dashboard that clearly displays key vulnerability data and trends. This allows your team to monitor and manage vulnerabilities effectively, with real-time updates that keep you informed of the current security status.

- Scalability and Flexibility
As your organization grows, your vulnerability management needs will evolve. Choose a tool that offers:
- Scalability: The ability to handle an increasing number of assets and vulnerabilities. The tool should be able to scale with your organization’s growth and adapt to new security challenges.
- Performance: Ensure that your vulnerability management system maintains performance efficiency as your organization expands. Scalability should not come at the expense of performance, so the tool must be capable of managing growth without compromising its effectiveness.
Example: YODA’s scalable architecture allows it to grow seamlessly with your organization. As your asset base expands and new security challenges arise, YODA effectively manages an increasing number of assets and vulnerabilities without compromising performance.
Conclusion
Understanding why vulnerability management is important and how to choose the right vulnerability management tool is crucial for maintaining a secure IT environment. By focusing on features like continuous scanning, risk assessment, user-friendliness and scalability, you can select a tool that meets your organization’s needs and enhances your cybersecurity posture.
For a more detailed comparison of top vulnerability management tools and their capabilities, check out our article on the Top 10 Vulnerability Management Tools for Cybersecurity. This resource will provide you with additional insights to help you make an informed decision about the best vulnerability management tool for your organization.
