How to Disable Directory Listing: A Step-by-Step Guide for Beginners
Previously in our last article of this Vulnerability Remediation Step-by-Step Guide Series, we demonstrated how to fix PHP vulnerabilities and secure your systems effectively. In this edition, we will look at how to disable Directory Listing with the help of vulnerability scanning and remediation tools such as 8iSoft YODA. YODA is an SMB-friendly vulnerability management tool offering a suite of features designed to streamline the process, from smart AI-based solutions to automatic, continuous monitoring and easy KPI tracking with its user-friendly dashboard.
I. What is a Directory Listing Vulnerability?
Before attempting to fix any vulnerability, it’s important to first understand the essence of the vulnerability itself.
First, what is a directory? To define directory, it’s like a physical folder in a filing cabinet you use to keep your papers- except that it’s in your computer. Directory is a location on a computer server where files are stored.
Directory listing vulnerability refers to a security flaw in a web server that allows unauthorized users to view the contents of these directories on a website. This normally occurs when the web server fails to properly restrict access to directory listing. When directory listing is enabled, the web server displays a list of files and folders within a directory, exposing sensitive information like configuration files and user data to potential hackers.
II. Why You Need to Disable Directory Listing?
Directory listing affects you and your business in several critical ways:
- Exposure of Sensitive Information: Directory listing allows anyone with access to your website to view the contents of directories. With just a few clicks, they could uncover valuable information that can be exploited.
- Increased Risk of Data Breaches: With directory listing enabled, the risk of data breaches significantly increases. Hackers can easily identify and exploit vulnerabilities in exposed files or directories, leading to unauthorized access, data theft, and potentially devastating consequences for your business and your customers.
- Compromised Website Security: Directory listing provides attackers with more hacking opportunities, enabling them to map out your website’s directory structure and identify potential entry points for further exploitation. This compromises the overall security posture of your website and increases the likelihood of successful cyberattacks.
- Damage to Reputation: A security breach resulting from directory listing vulnerability can severely damage your business’s reputation and erode customer trust. The exposure of sensitive information reflects poorly on your organization’s commitment to security, potentially leading to loss of customers, revenue, and market credibility.
To further emphasize the severity of this vulnerability, let’s take a glimpse at a real-world example. Here is an example of two URLs that enable directory listing, identified by the vulnerability remediation tool YODA:
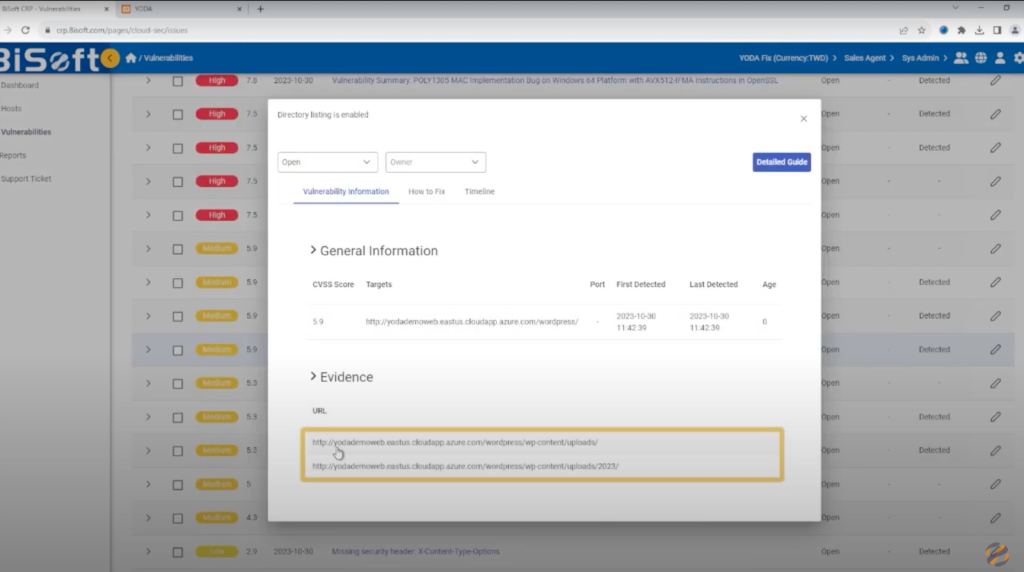

And this is what the link looks like when opened:
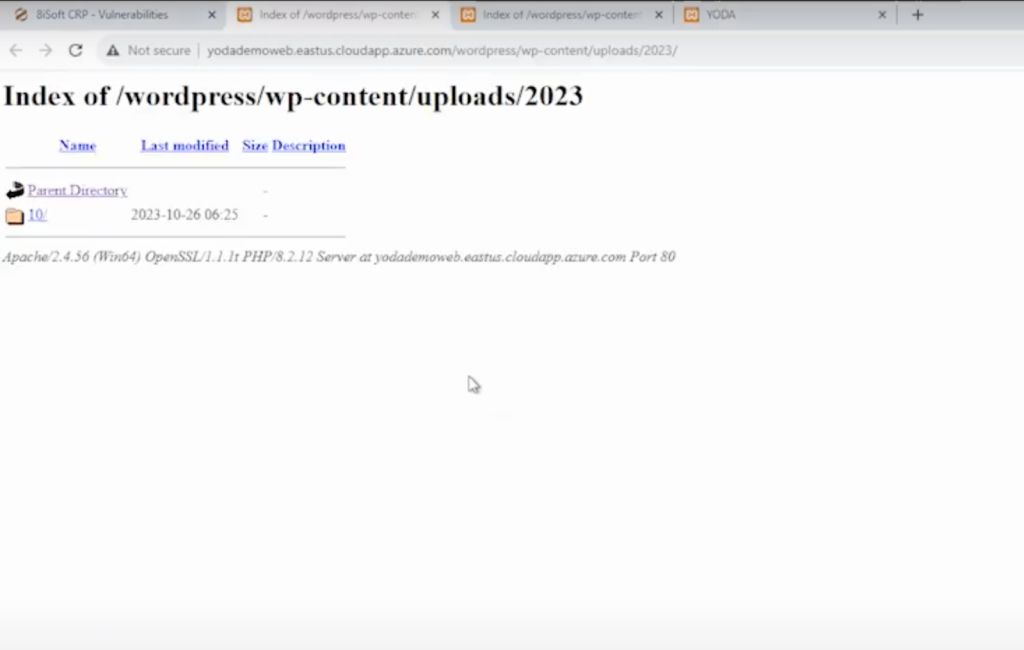

The links expose the website directory completely, providing unauthorized users with a detailed view of the directory structure, including file names, sizes and last modification dates. This exposure poses a significant security risk, as it enables hackers to gather valuable information about the website’s infrastructure and potentially exploit vulnerabilities present within the directory contents. To prevent unauthorized access and reduce any risks of data breaches, it is crucial to disable directory listing promptly.
III. How to Disable Directory Listing?
In this section, we will demonstrate the step-by-step process of disabling directory listing, utilizing the vulnerability management tool 8iSoft YODA. It’s important to note that the method to disable directory listing varies depending on the web server software you’re using. While YODA caters to various web server setups like Apache and Nginx, we’ll focus on Apache server for this demonstration.
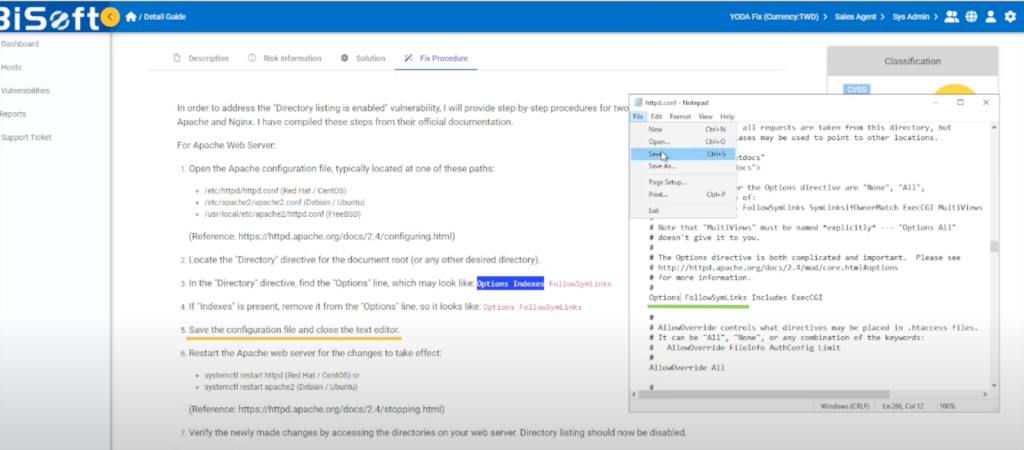
- Open the Apache configuration file
Begin by accessing your Apache server’s configuration file. This file is typically located in the /etc/apache2/ directory on Linux systems.
- Locate the ‘Directory’ directive
Within the configuration file, locate the “Directory” directive corresponding to the directory for which you wish to disable listing.
- Identify the problematic line enabling directory listing
Within the “Directory” directive block, look for the line containing “Options Indexes FollowSymLinks” or “Options +Indexes”. This is the line that enables directory listing. The line contains the “Options Indexes” directive, which instructs Apache to generate directory listings for that directory.
- Utilize YODA’s suggested keywords for a more efficient search
To expedite the search process, you can use YODA’s suggested keywords feature. Simply input relevant keywords related to directory listing vulnerabilities, and YODA will provide targeted suggestions to help you locate the problematic line more efficiently.
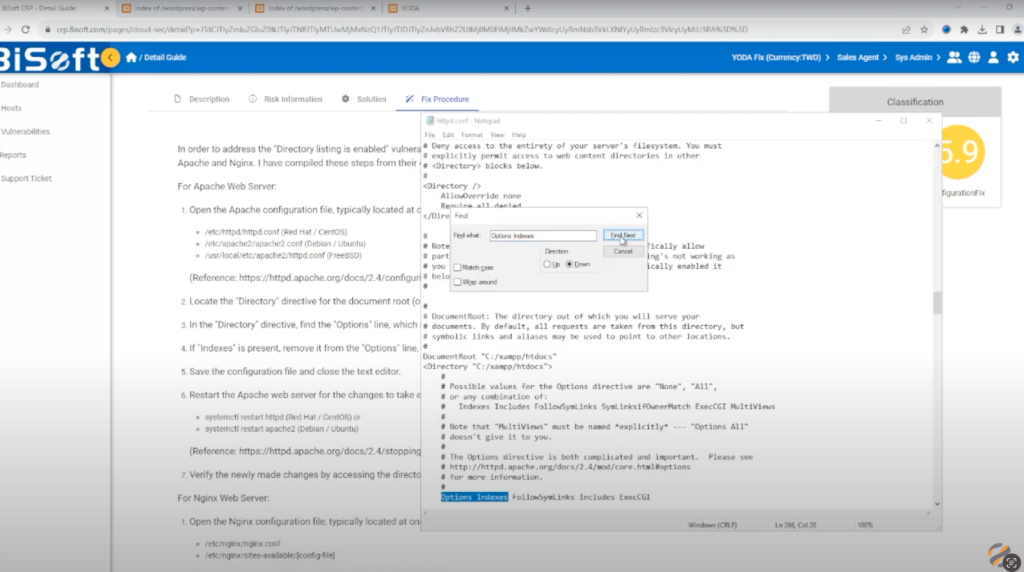

- Remove “Indexes” from the “Options” line
Delete “Indexes” from the line “Options Indexes FollowSymLinks” or “Options +Indexes”. By modifying to remove the “Indexes” option, you can disable directory listing for that specific directory.
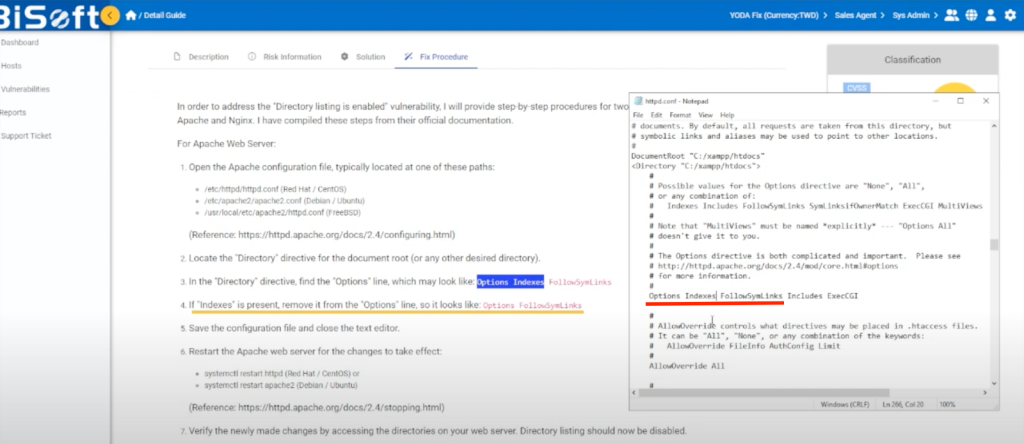

- Save and restart
After making the necessary modifications, save the configuration file and restart the Apache web server to apply the changes.

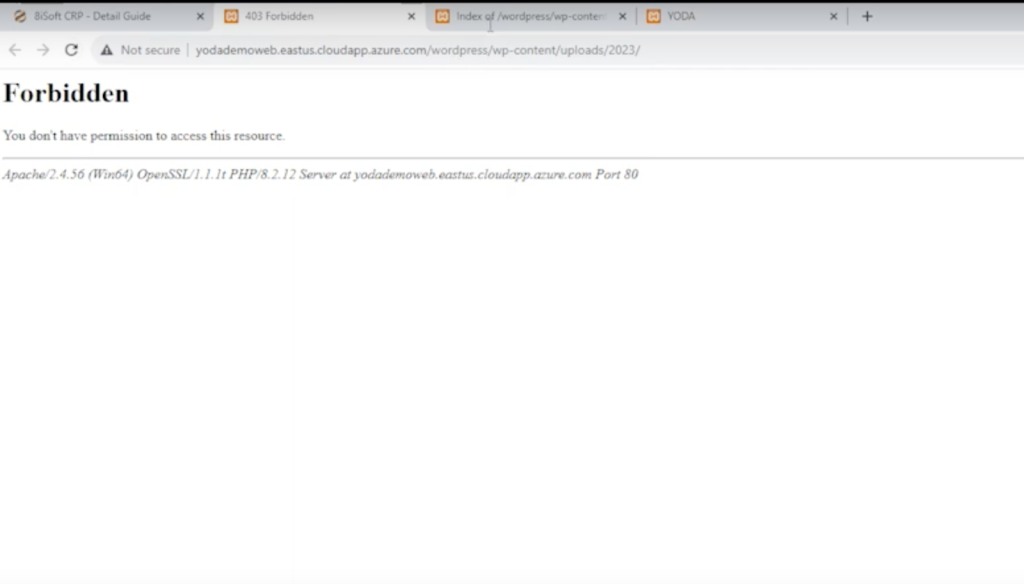
- Verify the fix
To make sure the fix was successful, try to open the links that previously displayed directory listing and confirm that it is now disabled. With directory listing disabled, you should receive a “403 Forbidden” error instead.

Following these steps ensures that your website is no longer susceptible to directory listing vulnerabilities. But don’t just take our word for it. Let’s verify the resolution using YODA.
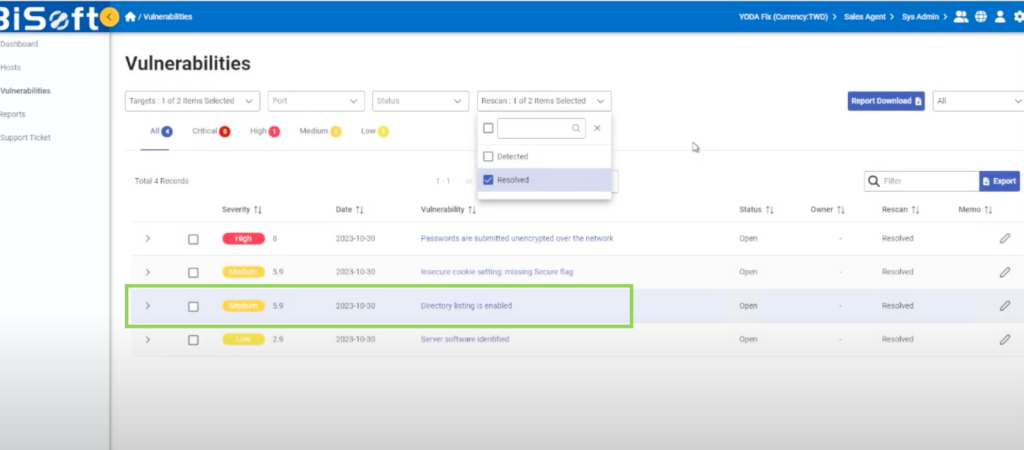
- Rescan with YODA
Open YODA and check the vulnerability status using the “Resolved” filter. Confirm that the directory listing vulnerability is no longer present by reviewing the detection times, evidence links, and the timeline view provided by YODA. This timeline shows the date and time when the directory listing vulnerability was first detected and when it was resolved, thus representing a clear demonstration that the vulnerability has been fixed.

With YODA, mitigating vulnerabilities like directory listing becomes a breeze. By following this step-by-step guide and leveraging 8isoft YODA’s vulnerability management tool, you can effectively disable directory listing and strengthen the security of your web server.
🎥 Watch the Tutorial: Disable Directory Listing with 8isoft YODA
Check out our video tutorial for a step-by-step guide on Disabling Directory Listing using 8iSoft YODA, and stay tuned for the next installment in our vulnerability remediation series, where we demonstrate the best practices for effective vulnerability management.
