The Crucial Role of ISO 27001 Certification in Managing Risk in the Technology Industry
Brief Overview of ISO 27001


ISO 27001, a global standard for robust cybersecurity and data protection, serves as both a formal certification and a best-practice framework. Acknowledged worldwide, it extends its applicability beyond IT to various industries, including pharmaceuticals, healthcare, energy, and services. Emphasizing confidentiality, integrity, and availability of information, ISO 27001 is essential for any organization handling sensitive data. In SaaS companies, its certification enhances credibility, making them a preferred choice for clients seeking reliable and secure services.
Benefits of ISO 27001 for the Software Industry
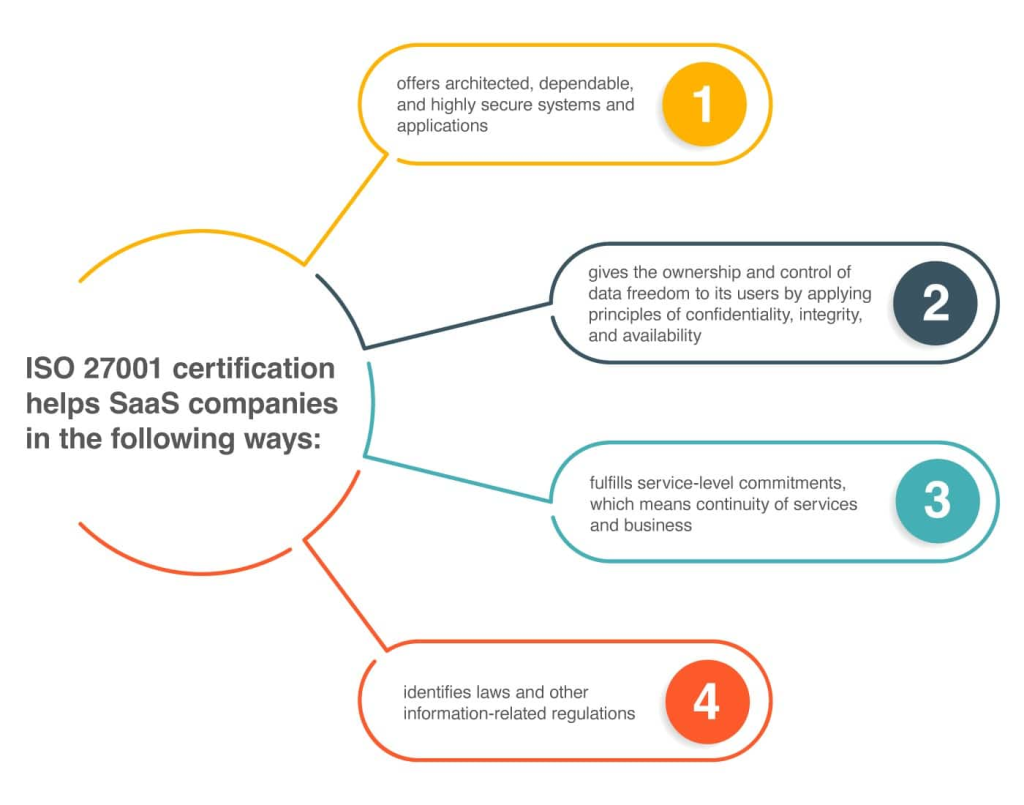
Beyond credibility, ISO 27001 certification offers operational efficiency, client retention, and competitive advantages. It is often a top security requirement for companies seeking dependable and secure systems. This certification involves applying principles like confidentiality and integrity, giving users control over their data. It aids in risk management, ensuring service continuity during disruptions, and prompts adherence to laws and regulations, reducing legal risks for clients.

II. Understanding NIST and its Relation to ISO 27001
NIST Overview
Purpose of NIST 800-53 and its Significance
NIST 800-53, developed by the National Institute of Standards and Technology, is a flexible cybersecurity standard and compliance framework. Regularly updated, it defines standards, controls, and assessments based on risk, cost-effectiveness, and capabilities. Crucial for federal information systems, government agencies, and contractors, NIST 800-53 provides a universal foundation for cybersecurity needs, covering a broad range of materials.

NIST CSF and its Role in Risk Management
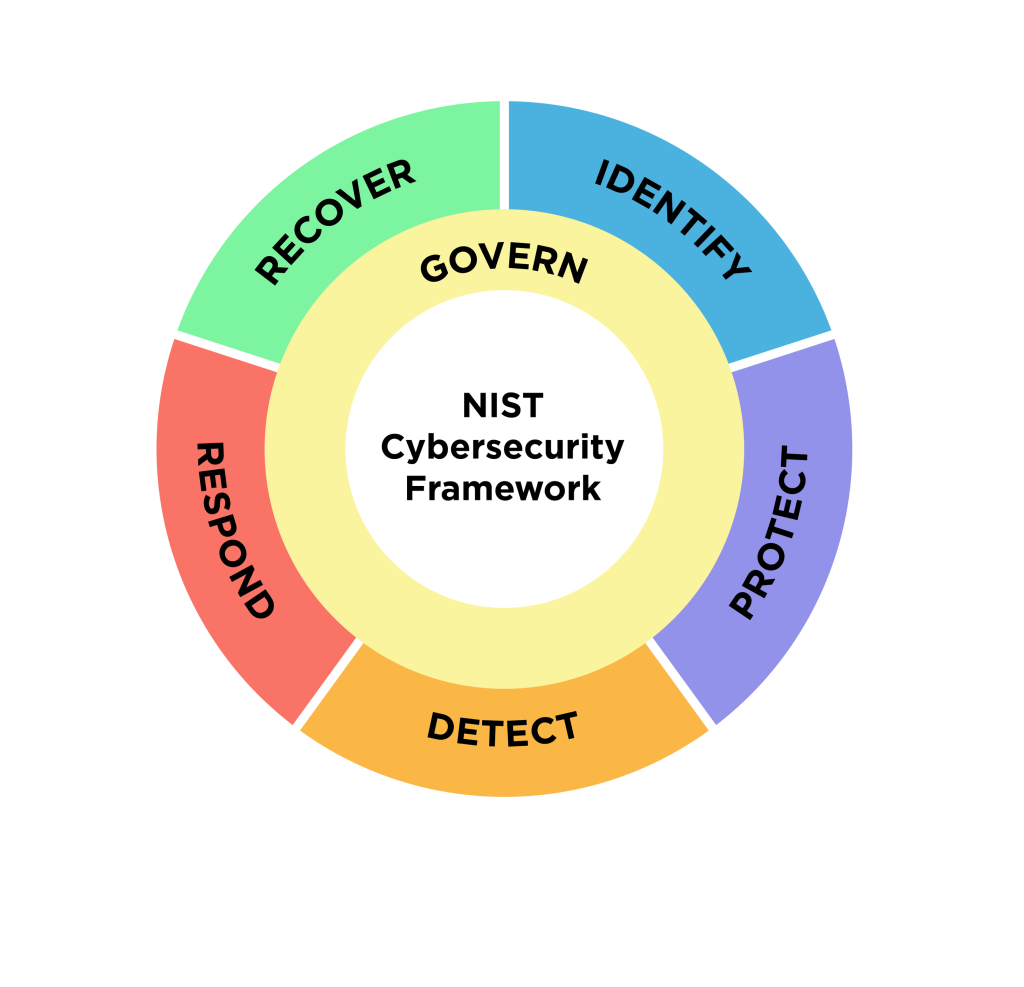
The NIST Cybersecurity Framework (CSF), initially designed for U.S. critical infrastructure, is now a global standard. Customized measures, based on industry standards and best practices, provide a common language across all organizational levels. The CSF’s five functions—Identify, Protect, Detect, Respond, and Recover—serve as an organized approach for assessing and managing cybersecurity risks.
NIST CSF vs. ISO 27001
Comparing NIST CSF and ISO 27001
NIST CSF and ISO 27001 are widely adopted safeguards for managing cybersecurity risks. While ISO 27001 focuses on improving information security management systems, NIST CSF aids in reducing risks for networks and data. Despite differences, both frameworks contribute to a robust security posture. Organizations holding ISO 27001 certification meet about 83% of NIST CSF requirements, and vice versa, making them complementary.
How NIST CSF Complements ISO 27001 in Risk Management
NIST CSF and ISO 27001 complement each other by sharing commonalities in their processes. NIST CSF provides a flexible, high-level framework, while ISO 27001 enhances technical aspects for comprehensive risk management. Starting with NIST CSF offers foundational understanding, integrating ISO 27001 enhances the management of evolving threats and regulatory demands.
III. The Framework of Risk Management (RMF)
Importance of a Risk Management Framework
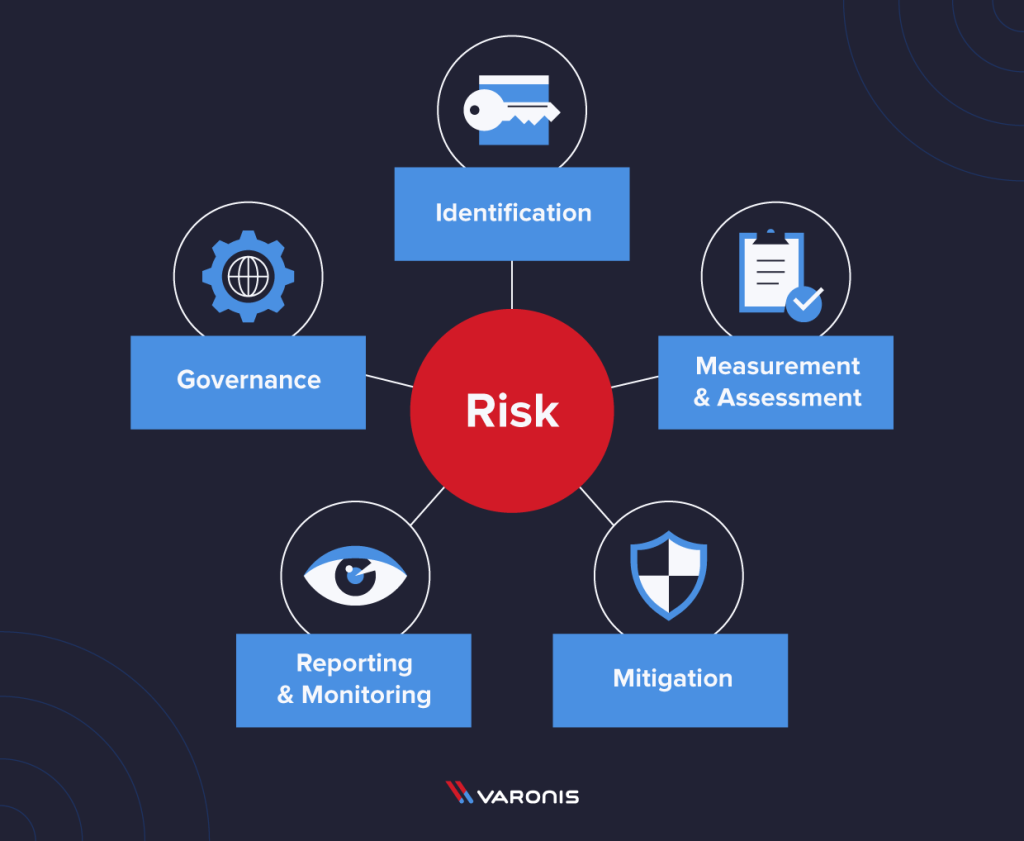
A Risk Management Framework (RMF) is vital for systematic risk handling and compliance in organizations. It includes steps like risk identification, assessment, analysis, control implementation, and continuous monitoring. Notable frameworks such as NIST RMF and COBIT offer structured approaches. Key components include governing risk, identifying and measuring impact, mitigating risks, and ongoing monitoring. Governance assigns responsibilities and establishes policies, while risk identification focuses on strategic and technology-related risks. Risk measurement assesses likelihood and impact, and mitigation involves implementing controls. Regular monitoring ensures effective risk management through a six-step process: setting objectives, defining tolerance, categorizing assets, conducting impact analysis, implementing controls, and reporting outcomes to leadership.

NIST’s Risk Management Framework (RMF)
Key Concepts of NIST RMF
NIST RMF, a comprehensive set of information security policies and standards, follows a risk-based approach in six systematic steps. This cyclical process ensures adaptability to changes in the environment or the system.
How NIST RMF and ISO 27001 Work Together
NIST RMF and ISO 27001 collaborate to safeguard organizations and their data. ISO 27001 aligns seamlessly with NIST RMF, signifying a commitment to robust measures for data protection. Achieving ISO 27001 accreditation is supported by comprehensive training courses, combining ISO 27001 Foundation and Lead Implementer courses.
IV. ISO 27001 Certification: A Vital Component in Risk Mitigation
The Significance of ISMS and ISO 27001 Certification
Establishing a Robust ISMS
A robust Information Security Management System (ISMS) is fundamental for safeguarding sensitive information. ISO 27001 certification, a globally recognized standard, is a testament to an organization’s commitment to maintaining information security, including confidentiality, integrity, and availability.
Achieving ISO 27001 Certification
Phases of ISO 27001 Certification
The certification process involves creating a project plan, determining the ISMS scope, performing a risk assessment, and gap analysis. Subsequent phases include policy and control implementation, employee training, and evidence documentation. The final stages involve completing the certification audit, continuous compliance through surveillance audits, and a recertification audit after three years.
Key Requirements and Considerations of ISO 27001
Organizations must navigate key requirements, starting with a project plan and defining the ISMS scope. A formal risk assessment and gap analysis precede the design and implementation of policies and controls. Employee training, documentation, and evidence collection contribute to preparing for the certification audit. Continuous compliance, internal audits, and a recertification audit ensure the ISMS remains effective.
V. Benefits of ISO 27001 Certification in the Technology Industry
ISO 27001 certification offers significant advantages for SaaS companies in the technology industry. Enhanced data security, trustworthy systems, and risk management contribute to increased customer trust, retention, and acquisition. Fulfilling service-level commitments ensures business continuity, and legal compliance mitigates risks for SaaS companies, positioning them as credible and committed to secure and reliable services.
VI. Common Challenges in Obtaining ISO 27001 Certification
- Complexity of ISO 27001 Standard: Navigating the intricate requirements, controls, and processes of the ISO 27001 standard can be challenging for organizations new to the standard.
- Cultural Shift and Employee Training: Implementing ISO 27001 requires a cultural shift, necessitating comprehensive training programs to ensure employee understanding and adherence to new security protocols.
- Alignment of Existing Practices: Aligning current organizational practices with ISO 27001 requirements poses a challenge, requiring modification of existing processes to meet the standard’s criteria.
- Documentary and Record-Keeping Demands: ISO 27001 demands meticulous documentation, posing a challenge for organizations in terms of maintaining accurate and comprehensive records.
- Ongoing Commitment and Resource Allocation: ISO 27001 compliance requires a continuous commitment and resource allocation for ongoing compliance as the security landscape evolves and new risks emerge over time.
