Introduction
In the dynamic landscape of technology startups, the surge in new ventures, particularly during the global pandemic, has been unprecedented. With over 550 million applications to establish businesses in the United States alone in 2020, startups face numerous challenges, from limited resources to cybersecurity vulnerabilities. In this digital era, where data breaches are on the rise, it becomes imperative for IT startups to prioritize their cybersecurity defenses. One effective way to achieve this is through the adoption of vulnerability management software.
Section 1: The Changing Face of Cybersecurity Threats
In today’s digital realm, cyber threats are constantly evolving, growing more sophisticated by the day. Startups, with their innovative approaches but limited resources, become prime targets for hackers. According to the Verizon Data Breach Investigations Report (2021), 46% of data breaches target small businesses, including startups. Enter vulnerability management software, a proactive shield that continuously scans for potential issues, ensuring startups can safeguard their data, customer information, and intellectual property.


Section 2: Preserving Reputation and Customer Trust
A startup’s reputation is paramount for success, and a security breach can have severe repercussions. A Kaspersky survey (2021) reveals that 50% of customers would cease using a company’s services after a data breach. Vulnerability management software not only protects sensitive information but also demonstrates the startup’s commitment to cybersecurity. By proactively securing systems, startups build trust, enhance their reputation, and attract more customers and investors.

Section 3: Ensuring Regulatory Compliance for Startups
Compliance with industry regulations is non-negotiable for startups aiming to avoid legal troubles and maintain credibility. Failure to adhere to data protection laws can lead to hefty fines. Vulnerability management software provides insights into security, helping startups meet regulatory requirements. It ensures that the startup stays on the right side of the law, reducing the risk of compliance violations.


Section 4: The Cost of a Data Breach for Startups
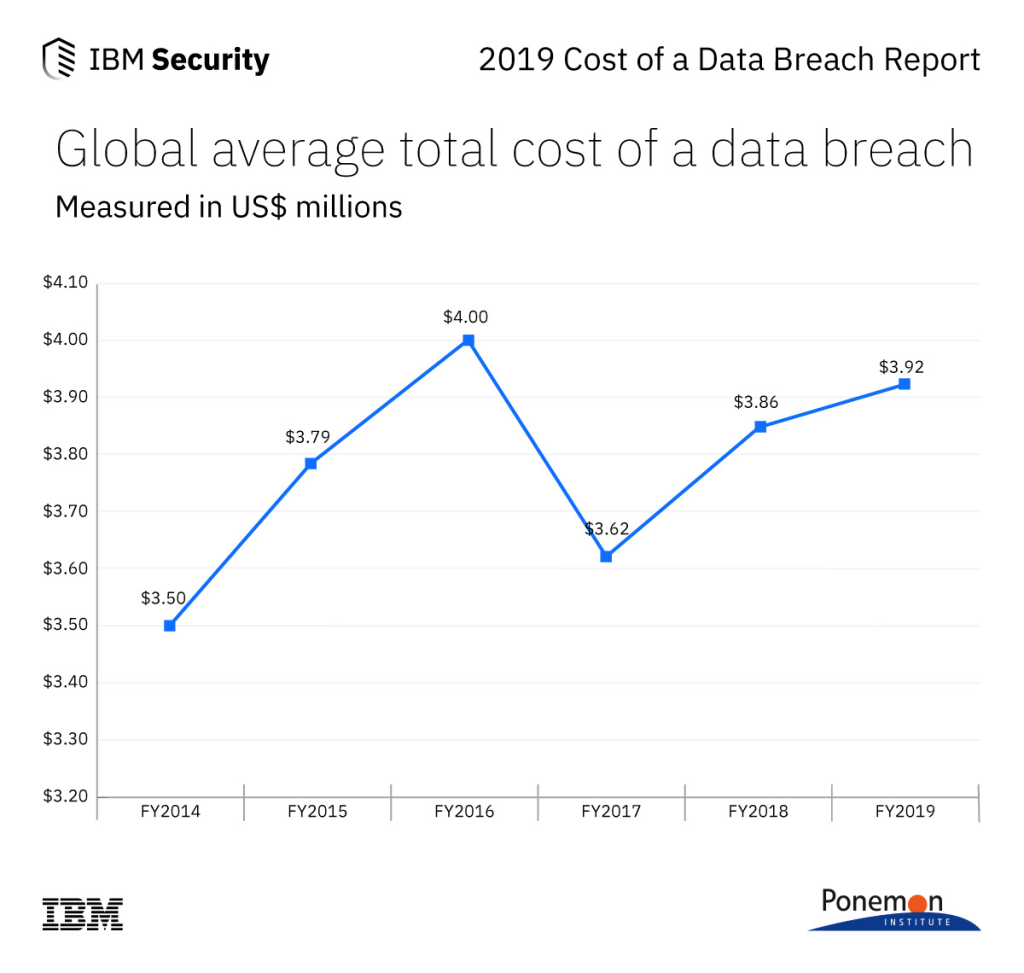
The financial impact of a data breach can be devastating for startups. In 2023, IBM reported that the average cost of a data breach for small-scale organizations (<500 employees) increased from $2.92 million to $3.31 million in the last year. To mitigate this risk, investing in vulnerability management software is a proactive and cost-effective approach. This software acts as a shield, helping startups avoid significant financial losses, repair their reputation, and recover from potential breaches.

Section 5: A Side-by-Side View of Vulnerability Management Software
Introducing 8iSoft YODA
8iSoft YODA is a startup-friendly solution designed to prevent data leaks and bolster cybersecurity. Following a three-part framework – Discovery, Remediation, and Improvement (DRI) – 8iSoft YODA ensures comprehensive scanning, assessment, and protection of networks. With step-by-step remediation methods, scalable options, and transparent pricing, 8iSoft YODA caters to the security needs of startups, making it an accessible and effective choice.
| Features | Acunetix By Invicti | Tenable Nessus Vulnerability Management | Qualys Vulnerability Management (VMDR) | Rapid7 Insight VM | 8iSoft YODA |
|---|---|---|---|---|---|
| Vulnerability Scanning | ✓ | ✓ | ✓ | ✓ | ✓ |
| Audit Reports | ✓ | ✓ | ✓ | ✓ | ✓ |
| Compliance Report | ✓ | ✓ | ✓ | ✓ | ✓ |
| Knowledge Database | ✓ | ✓ | ✓ | ✓ | |
| Step by Step remediation | ✓ | ||||
| Role-based access control (RBAC) | ✓ | ✓ | ✓ | ✓ | ✓ |
| Admin/ Users System | ✓ | ✓ | ✓ | ✓ | ✓ |
| Minimum Assets | N/A | 65 | 32 | 250 | 5 |
| Official Site On-demand Purchase | No | Yes | No | No | Yes |
| Starting Price (/month) | Contact for Quotes | $278.29 USD | Contact for Quotes | $547.50 USD (AWS Marketplace) | $128 USD |
| Ideal Audience | Batch scanner for large enterprises ($$$) | Batch scanner for large enterprises ($$$) | Targets large range of audiences ($$-$$$) | Looking at midsized enterprises ($$) | Accessible for small companies, scalable for larger enterprises ($-$$) |
Ready to Start?
Get 8iSoft Yoda now or receive our free sneak peak vulnerability assessment report!
